Contents
- 1 News & Tools
- 2 Google: My Activity
- 3 Anti-Virus, or Not?
- 4 ICMP (Internet Control Message Protocol)
- 5 Mask vs Default Mask
- 6 Classful Addressing vs Classless Addressing
- 7 Deducing Class B range
- 8 Powers of 2
- 9 Subnetting Tutorial & Reference Page
- 10 Supernetting
- 11 Subnetting
- 12 Subnetting Tips/Notes
- 13 IP: Total Addresses vs. Usable Addresses
- 14 Wildcard Mask (a.k.a. Inverse Mask)
- 15 Determine the Network Address
- 16 Block Size
- 17 Read / Do / Watch
- 18 Do: Assignment #1
- 19 Do
- 20 Do
- 21 Better Focus and Efficient Studying When Not Multitasking
News & Tools
- picoCTF is a free computer security education program with original content built on a capture-the-flag framework created by security and privacy experts at Carnegie Mellon University.
- What Does It Actually Mean When a Company Says, “We Do Not Sell Your Data”?
- Stolen Credentials Led to Data Theft at United Nations
- Google’s FLoC Is a Terrible Idea (EFF)
- Decentralized Autonomous Organization (DAO)
- Evolved phishing: Device registration trick adds to phishers’ toolbox for victims without MFA
- Windows 10 quietly got a built-in network sniffer, how to use
- Study reveals Android phones constantly snoop on their users
- Unpatched Android App with 1 Billion Downloads Threatens Spying, Malware: Attackers can exploit SHAREit permissions to execute malicious code through vulnerabilities that remain unpatched three months after app makers were informed.
- Breaking Into a Smart Home With A Laser – Smarter Every Day 229
- This work was performed by a team of researchers at the University of Michigan and University of Electro-Communications in Japan.
- For more information check out their website http://lightcommands.com or contact them at [email protected]
- ‘The intelligence coup of the century’ : For decades, the CIA read the encrypted communications of allies and adversaries. By Greg Miller
- Microsoft Buys Corp.com So Bad Guys Can’t by KrebsOnSecurity.com
- Open Source Security: Episode 184 – It’s DNS. It’s always DNS
- Dangerous Domain Corp.com Goes Up for Sale by Brian Krebs
- Microsoft Security Response Center: MS15-011 & MS15-014: Hardening Group Policy
- VFEmail suffered catastrophic data destruction at the hands of external threat actor:
BlueBorne
- The IoT Attack Vector “BlueBorne” Exposes Almost Every Connected Device
- BlueBorne is an attack vector by which hackers can leverage Bluetooth connections to penetrate and take complete control over targeted devices.
- BlueBorne affects ordinary computers, mobile phones, and the expanding realm of IoT devices.
- The attack does not require the targeted device to be paired to the attacker’s device, or even to be set on discoverable mode.
Google: My Activity
- See the logs of what you’ve searched for, visited, and watched on Google services.
Anti-Virus, or Not?
- In my opinion, anyone who promotes not using anti-virus and other protective software on all computers and devices connected to the Internet is irresponsible, to your systems, and also to others on the Internet. It is too trivial for systems to be compromised by malware.
ICMP (Internet Control Message Protocol)
The Internet Control Message Protocol (ICMP) is one of the core protocols of the Internet Protocol Suite.
- ICMP works at the Network layer and is used by IP for many different services. ICMP is basically a management protocol and messaging service provider for IP.
- ICMP messages are encapsulated within IP datagrams.
- ICMP is used by network devices, like routers, to send error messages indicating, for example, that a requested service is not available or that a host or router could not be reached.
- Destination unreachable:
If a router can’t send an IP datagram any further, it uses ICMP to send a message back to the sender, advising it of the situation. - For example, take a look at Figure 3.17, which shows that interface E0 of the Lab_B router is down.
- Destination unreachable:
- ICMP can also be used to relay query messages.
- ICMP is assigned protocol number 1.
- ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute).
ICMP messages are divided into two broad categories: error-reporting messages and query messages.
- The error-reporting messages report problems that a router or a host (destination) may encounter when it processes an IP packet.
- The query messages, which occur in pairs, help a host or a network manager get specific information from a router or another host.
- For example, nodes can discover their neighbors. Also, hosts can discover and learn about routers on their network, and routers can help a node redirect its messages.
When a packet is received by a router, what does the router have to do?
- Decrement TTL by 1, then evaluate TTL
- The router will decrement TTL by 1, then evaluate the value of TTL to determine if the packet should be dropped or forwarded.
- If TTL = 0, then drop the packet and send an ICMP destination unreachable to the sender
- If TTL > 0, then proceed
- What is the network that the packet is destined for?
- Do I have that network in my routing table?
- If no, then drop the packet and send an ICMP destination unreachable to the sender
- If yes, then…
- Which interface of mine do I have to send the packet out of to get it to the destination network?
- What is the IP address of the next closest router that I have to send the packet to? (Next Hop IP)
- Forward the packet to the destination network via the next hop router.
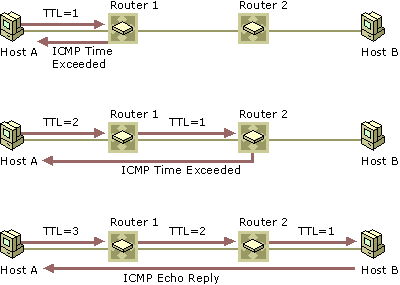
Traceroute
- Traceroute is a diagnostic command that uses ICMP and TTL to map a path to the destination IP address:
Mask vs Default Mask
What is the Default Mask?
- The “Default Mask” is when there is not subnetting or supernetting.
- Classful Addressing is when the “Default Mask” is used.
- The “Mask” is not the same as “Default Mask” if the subnet masks are not Class A, B, or C.
Classful Addressing vs Classless Addressing
Classless Addressing is when we’re not using a classful mask. e.g. Class A, B, or C
IP Address Classes (IP v4)
| Class | From | To | No. of Networks | Hosts per Network | High Order bits | Network Number bits | Host Number bits |
| A | 1.0.0.0 | 126.255.255.255 | 126 | 16,777,214 | 0000 | 0-7 | 8-31 |
| B | 128.0.0.0 | 191.255.255.255 | 16,384 | 65,534 | 1000 | 1-15 | 16-31 |
| C | 192.0.0.0 | 223.255.255.255 | 2,097,152 | 254 | 1100 | 2-24 | 25-31 |
127.x.y.z is a reserved address range used for the local loopback and diagnostics.
Deducing Class B range
- We know 127.0.0.1, is the loopback address, and the 127.0.0.0 range is reserved, and is never assigned to hosts.
- We’re familiar with 192.168.0.0 Class C. And Class C start with 192.0.0.0
- So, Class B, start and 128.0.0.0, and ends before Class C at 191.255.255.255
- And, Class A, starts a 1.0.0.0 and ends before the 127.0.0.0 address, at 126.255.255.255
Powers of 2
(CCNA Certification Study Guide, p. 79)
- Each successive power of 2 is double the previous one.
- Total number of subnets, must be a power of 2
- Total number of addresses per subnet, must be a power of 2
- Total number of addresses in a block of addresses, must be a power of 2
- All IP address blocks must be divided on boundaries of power of 2.
- All subnets are “contiguous.”
- Contiguous means: touching or connected throughout in an “unbroken sequence.”
- Contiguous is not restricted to VLSM, although the text book may only use that specific term in relation to VLSM
- Our experience when subnetting is all the subnets we derived were consecutive with no gaps.
- The exponent will be the number of bits used for either the network portion or the host portions of an IP address.
Subnetting Tutorial & Reference Page
- Subnetting Cross-Reference chart
- The “interesting octet” is the last octet in the mask, from left to right, with bits turned on.
- Block Size is the Subnet Increment, not the number of addresses per subnet.
- Using the AND function to determine the network address
- Wildcard Mask
- Broadcast Address
Supernetting
- Combines contiguous networks to create a larger block of addresses
- Decreases the number of 1’s in the mask
- (i.e. Decreases the number of “network” bits, and increases the number “host” bits)
Subnetting
- Divides an address block into smaller networks
- Increases the number of 1’s in the mask
- (i.e. Increases the number of “network” bits, and decreases the number “host” bits)
Answer these questions when subnetting:
- How many subnets are needed?
- How many “total addresses” per subnet are needed?
- How many network are bits used?
- How many host are bits used?
- What are the valid subnets?
- What’s the broadcast address for each subnet?
Subnetting Tips/Notes
- If no mask/prefix is given, then borrow bits starting from the “Class” boundary of the IP address.
- If a mask/prefix is given, then the given mask/prefix is the result of subnetting. (Borrow bits from the “Class” boundary to the given mask/prefix.) (e.g. Q. 7, Pg. 40)
- The total number of subnets and total number of hosts must be a power of 2.
- Is the question asking for “subnets” or “hosts”
- If you’re asked for the # of hosts, then you must determine how many bits are needed to get that # of hosts, then subtract those bits from the 32 IPv4 bits, to determine the network bits / mask / prefix.
- Determine the number of subnets: 2[number of bits borrowed].
- Determine the total number of addresses: 2[the number of host bits].
- Add the Wildcard mask to the network/subnet address to determine the broadcast/last address in the network/subnet.
- Block Size:
- The block size (256 – [The interesting octet]) is best used to determine the increment of the subnets.
- The interesting octet is the last octet, from the left, that you borrowed bits from.
- The “block size” is not the number of addresses per subnet. It is the increment from one subnet to the next, within the “interesting” octet.
- Determine how many addresses to add to the network address/subnet zero to get to the target subnet.
- 1. Multiplying (Subnet “Number”) by the (number of addresses per subnet).
(For the Nth subnet, subtract 1 before multiplying by the number of addresses per subnet.) - 2. Convert the result to its Base-256 equivalent
- 3. Add the Base-256 equivalent to the original network address of the block to get the network/subnet address of the target subnet.
- 1. Multiplying (Subnet “Number”) by the (number of addresses per subnet).
- The “subnet address” is the same as the “network address” of a subnet.
- Subnet using the methods that work for all subnets, large or small. Switching methods depending on the size of the subnet requires more effort than is necessary.
- Practice makes improvement!
- Subnetting Notes:
- Pay attention to whether the customer needs “networks” or “hosts”
- If the prefix/mask is given, and either the required number of subnets, or the required number of host addresses, then the prefix/mask is our starting point. (Start borrowing bits after the given prefix)
- If only the Network Address and a Prefix are given, then the given prefix is the result of an already subnetted network. Since we’re not given any other information, we’ll have to use the “class” of the Network Address as the starting point, before subnetting, and then borrow the number of bits needed to match the given prefix.
- The nth subnet range, includes the subnet network IP address and the broadcast IP address. e.g. 192.168.1.0 to 192.168.1.25
- The subnet number for the nth subnet, is the 1st address in the nth subnet. e.g. Network ID / Subnet address / Network address for the nth subnet.
IP: Total Addresses vs. Usable Addresses
- We must always determine the total number of addresses first.
- Then, if asked, we may subtract 1 for the network address and 1 for the broadcast address.
- Never, ever, automatically subtract 2
Wildcard Mask (a.k.a. Inverse Mask)
- In subnetting/supernetting, the wildcard mask is the number of total addresses within a subnet, (minus 1).
- In subnetting/supernetting, the wildcard mask allows you to determine the broadcast address of a subnet, by adding the wildcard mask to the network address.
- Each octet of the Subnet mask + the corresponding Wildcard mask adds up to 255.
- Example: Subnet mask of 255.255.240.0, yields a wildcard mask of 0.0.15.255.
- Example: Subnet mask of 255.255.255.224, yields a wildcard mask of 0.0.0.31.
Determine the Network Address
Block Size
- The Block Size is the increment from one subnet to the next subnet.
- The Block Size is NOT the number of addresses per subnet!!!!
- The “interesting octet” is the last octet, from the left, with bits turned on.
- 256 – the interesting octet = Block Size
The block size/subnet increment can also be determined by the bit position of the “interesting octet” of the mask.
| Bit position | 1 bit | 2 bits | 3 bits | 4 bits | 5 bits | 6 bits | 7 bits | 8 bits |
| Value of bit position/Block Size | 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
~
Read / Do / Watch
CCNA Certification Study Guide, Volume 2
- Read Chapter 5: IP Routing
- Do the Written Labs
- Answer the Review Questions
- Do not submit your answers for this chapter. The answers are in Appendix.
Do: Assignment #1
- Due before Tues. Feb. 22, 2022, before 6pm EST.
- Download Assignment #1
- Important: Make sure to read and understand the instructions on how to handle the protected PDF
- If you have any issues completing all parts of every question on the assignment, e-mail me with the question # and the specifics you need assistance with.
- No late assignments will be accepted.
Do
- Memorize these Bit Patterns of Often Used Subnet Mask Values (pdf)
Do
Make sure to always have access to a calculator which has an Exponent function (^key) ( xy ) for every class.
