Contents
- 1 News & Tools
- 2 Subnetting Tutorial & Reference Page
- 3 Standards
- 4 Subnet zero and the all-ones subnet
- 5 Dynamic Host Configuration Protocol (DHCP)
- 6 ARP (Address Resolution Protocol)
- 7 Neighbor Discovery Protocol (NDP)
- 8 Subnetting Tutorial & Reference Page
- 9 Read / Watch / Do
- 10 Subnetting Tutorial & Reference Page
- 11 Do
- 12 Better Focus and Efficient Studying When Not Multitasking / Multi-Focusing
News & Tools
- How to study effectively: Forget cramming, ditch the highlighter, and stop passively rereading. The psychology of learning offers better tactics. by Paul Penn
- The Universe is Hostile to Computers (Veritasium)
- Amazon Sidewalk is LIVE – Opt Out Now! – ThreatWire
- [Re-post] HakTip – How to Capture Packets with Wireshark – Getting Started
- Hacker Tries to Poison Water Supply of Florida Town – A threat actor remotely accessed the IT system of the water treatment facility of Oldsmar and raised the levels of sodium hydroxide in the water.
- Hard-to-detect credential-theft malware has infected 1,200 and is still going
- The 5 Challenges of Detecting Fileless Malware Attacks
- RouterSecurity.org focuses on the security of routers.
- PrivacyTools.io provides knowledge and tools to protect your privacy against global mass surveillance.
Subnetting Tutorial & Reference Page
Standards
- RFC (Request for Comments)
- IEEE (Institute of Electrical and Electronics Engineers)
- Deprecated / Deprecation
Subnet zero and the all-ones subnet
- The first subnet obtained from subnetting has all bits in the subnet bit group set to zero (0). It is therefore called subnet zero.
- The last subnet obtained from subnetting has all bits in the subnet bit group set to one (1). It is therefore called the all-ones subnet.
- The IETF (Internet Engineering Task Force) discouraged the production use of these two subnets at one point due to possible confusion of having a network and subnet with the same address. The practice of avoiding subnet zero and the all-ones subnet was declared obsolete in 1995 by RFC 1878.
- In this class, we will always include subnet zero when we subnet.
Dynamic Host Configuration Protocol (DHCP)
- The process a host uses to get an IP address lease from the DHCP server
- RFC 2131 (Appendix C: DHCP RFCs)
- In addition to an IP address, what additional parameters, if any, does a host need to get from the DHCP server?
- Subnet Mask
- Default Gateway
- DNS Server’s IP address
- DHCP Server uses the UDP port 67 (bootps) and DHCP client uses UDP port 68 (bootpc)
For Phases of DHCP Leasing an IP Address to a Client
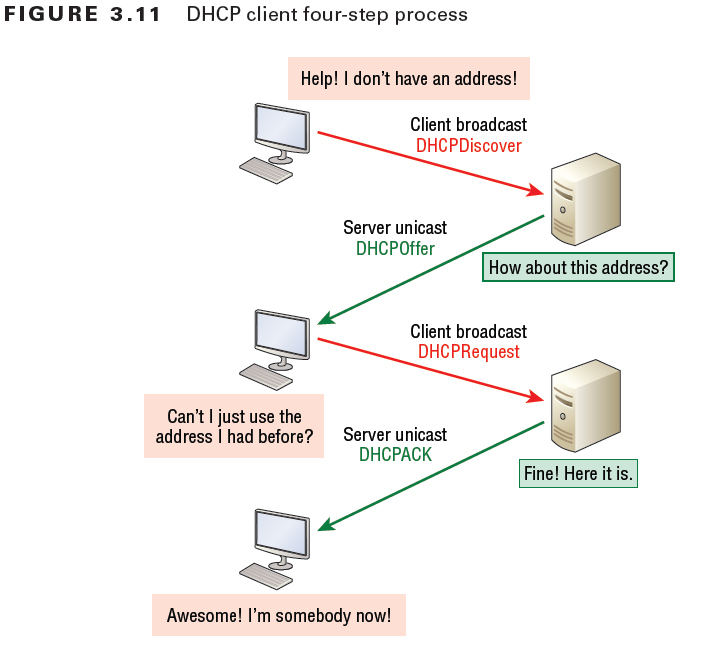
| Phase | Transmission Method | Description |
|---|---|---|
| Discover | broadcast –> | Client requests an IP address. The client broadcasts a DHCPDISCOVER message on the physical subnet to find available servers. The client creates a UDP packet with the broadcast destination of 255.255.255.255 or the subnet broadcast address. |
| Offer | <– unicast | DHCP server offers an IP address from its pool. When a DHCP server receives an IP lease request from a client, it extends an IP lease offer. This is done by reserving an IP address for the client and sending a DHCPOFFER message across the network to the client. This message contains the client’s MAC address, followed by the IP address that the server is offering, the subnet mask, the lease duration, and the IP address of the DHCP server making the offer. |
| Request | broadcast –> | When the client PC receives an IP lease offer, it must tell all the other DHCP servers that it has accepted an offer. To do this, the client broadcasts a DHCPREQUEST message containing the IP address of the server that made the offer. When the other DHCP servers receive this message, they withdraw any offers that they might have made to the client. They then return the address that they had reserved for the client back to the pool of valid addresses that they can offer to another computer. Any number of DHCP servers can respond to an IP lease request, but the client can only accept one offer per network interface card. |
| Acknowledge | <– unicast | When the DHCP server receives the DHCPREQUEST message from the client, the final phase of the configuration process is initiated. The acknowledgement phase involves sending a DHCPACK packet to the client. This packet includes the lease duration and any other configuration information that the client might have requested. At this point, the IP configuration process is complete. |
- DHCP: How a client handles errors.
- DHCP Scope: A Dynamic Host Configuration Protocol (DHCP) scope is the consecutive/contiguous range/sequence of possible IP addresses that the DHCP server can lease to clients on a subnet. Scopes typically define a single physical subnet on your network to which DHCP services are offered. Scopes are the primary way for the DHCP server to manage distribution and assignment of IP addresses and any related configuration parameters to DHCP clients on the network.
ARP (Address Resolution Protocol)
- Why is ARP on Layer 2 and not on Layer 3 of the OSI Reference Model?
- ARP provides a service to Layer 3
- ARP does not provide Layer 3 services.
- ARP does not use Layer 3 services.
- ARP is not exclusive to IP. ARP is used by other protocols
- ARP is definitely a layer 2 protocol, with Ethernet type = 0x806
- If anyone claims that ARP is on Layer 3, ask them: Does ARP have an IP protocol number?
- ARP/RARP
- ARP Spoofing
- ArpON: Defending against ARP Poisoning / ARP Spoofing
- XArp – Advanced ARP Spoofing Detection
Wireshark decode of an ARP Request packet:

WireShark decode of an ARP Request packet
Neighbor Discovery Protocol (NDP)
- Neighbor Discovery Protocol (NDP) performs functions for IPv6 similar to the way Address Resolution Protocol (ARP) and ICMP Router Discovery and Router Redirect protocols do for IPv4.
Subnetting Tutorial & Reference Page
- Subnetting Cross-Reference chart
- The “interesting octet” is the last octet in the mask, from left to right, with bits turned on. i.e. 1
- Block Size is the Subnet Increment, not the number of addresses per subnet.
- Using the AND function to determine the network address
- Wildcard Mask
- Broadcast Address
Read / Watch / Do
CCNA Certification Study Guide, Volume 2
- Read Chapter 4: Troubleshooting IP Addressing
- Do the Written Labs
- Answer the Review Questions
- Do not submit your answers for this chapter. The answers are in the Appendix.
- How to study effectively: Forget cramming, ditch the highlighter, and stop passively rereading. The psychology of learning offers better tactics. by Paul Penn
Subnetting Tutorial & Reference Page
OSI Reference Model {re-post}
- Study the: OSI Model Quick Reference (pdf)
- TCP/IP and the OSI Model Explained by Blanchae
- The OSI Model Demystified by Eli the Computer Guy
- Understanding the OSI Reference Model: Cisco Router Training 101 by SoundTraining.net
Do
Make sure to always have access to a calculator which has an Exponent function (^key) ( xy ) for every class.
