Contents
News & Tools
- SANS New2Cyber Summit 2022 Free Virtual Summit: March 23-24, 2022
- If you know someone who is new to cybersecurity or if you want to get a better idea of what its like for someone new to cybersecurity. This conference is a MUST ATTEND. share widely, broadly, and consider supporting it.
- Learning cyber security on TryHackMe is fun and addictive. Earn points by answering questions, taking on challenges and maintain your hacking streak through short lessons.
- Simplify compliance with ByteChek’s advanced and easy-to-use compliance platform.
- DDoS Attack Size Breaks Historical Records – ThreatWire
- Sophisticated hackers snuck sleeper malware into nearly 30,000 Macs
- Clipping Silver Sparrow’s wings: Outing macOS malware before it takes flight
- CISA Orders Federal Agencies to Patch Exchange Servers
- How to Use an Old Router as a Wi-Fi Adapter (Wireless Bridge)
Exam-01 / Quiz-03 Debriefing
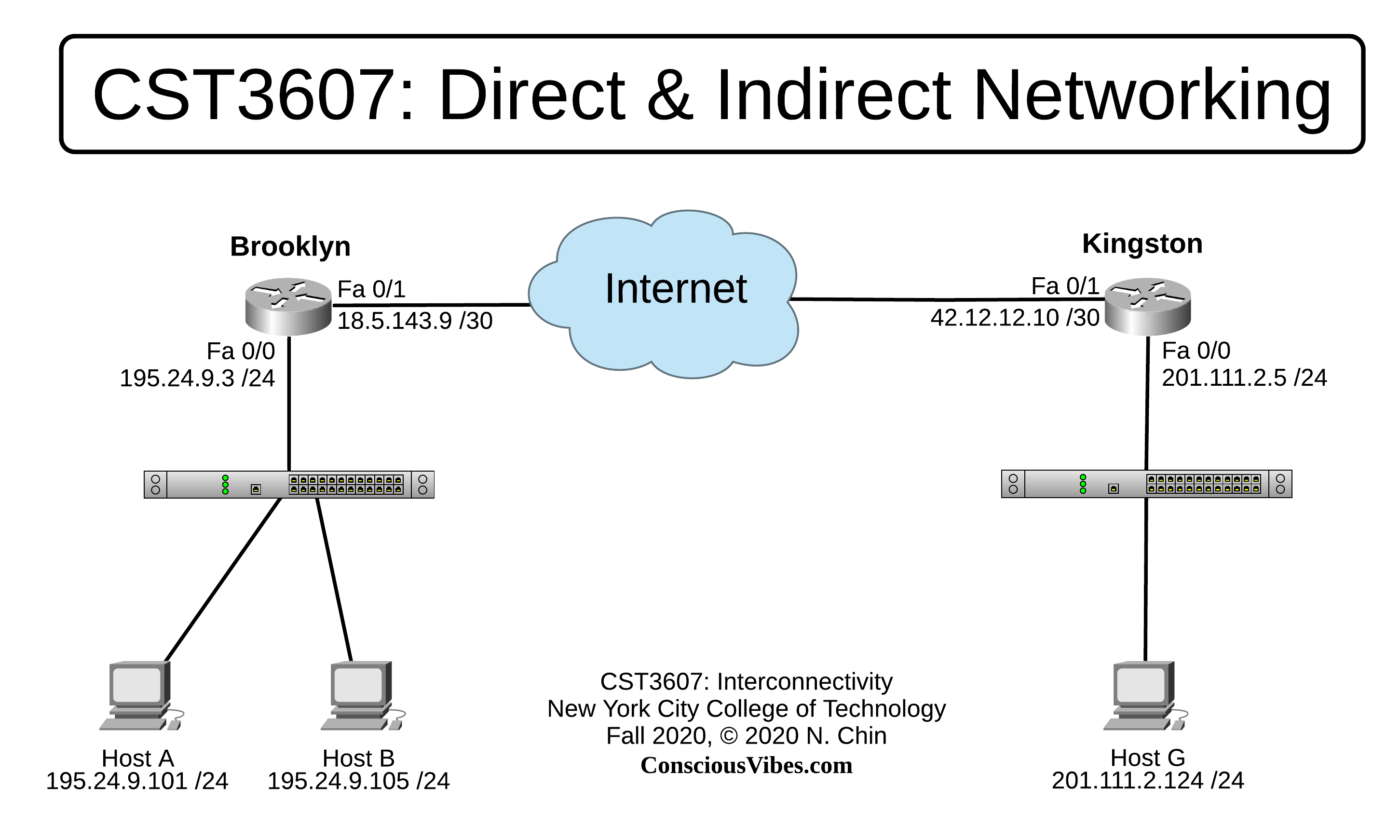
How Routers Talk to Each Other
Delivery of a Packet
- Direct Delivery
- Direct delivery occurs when the source and destination of the packet are located on the same physical network or when the delivery is between the last router and the destination host.
- Indirect Delivery
- If the destination host is not on the same network as the deliverer, the packet is delivered indirectly.
- In an indirect delivery, the packet goes from router to router until it reaches the one connected to the same physical network as its final destination.
- A delivery always involves one direct delivery but zero or more indirect deliveries.
- The last delivery is always a direct delivery.
Routing protocols
- A group of networks and routers under the authority of a single administration.
- The Internet is a network of networks; it’s broken up into hundreds of thousands of smaller networks known as autonomous systems (AS). Each of these networks is essentially a large pool of routers run by a single organization.
Convergence (routing protocol)
- In a converged network all routers “agree” on what the network topology looks like.
Metric
- A unit of measure used by routing protocol algorithms to determine the best pathway for traffic to use to reach a particular destination.
- Routers use various metrics and calculations to determine the best route for a packet to reach its final network destination.
- Each routing protocol uses its own algorithm with varying weights to determine the best possible path.
Routing Protocols
3 Routing Algorithms
There are 3 routing algorithms used by varying routing protocols to determine the router metrics. These algorithms are distance vector, link-state and path vector.
| Protocol Type | Characteristics | Examples |
| Distance-Vector | Uses hop count | RIP, IGRP, EIGRP IPX RIP |
| Link-State | Uses Shortest Path First, Common View of Network | NLSP, OSPF, IS-IS |
| Path Vector | Maintains the path information that gets updated dynamically. Updates looped through the network and returned to the same node are easily detected and discarded. | BGP (Border Gateway Protocol) |
An interior gateway protocol (IGP) is a routing protocol that is used within an autonomous system (AS).
Interior gateway protocols can be divided into two categories
- Distance-vector routing protocols
- e.g. RIP, IGRP, EIGRP
- A distance-vector routing protocol requires that a router inform its neighbors of topology changes periodically and, in some cases, when a change is detected in the topology of a network.
- Link-state routing protocols
- e.g. OSPF, Intermediate System to Intermediate System (IS-IS)
- link-state protocols require a router to inform all the nodes in a network of topology changes
An Exterior Gateway Protocol (EGP) is used between autonomous systems.
- Border Gateway Protocol (BGP) is the core routing protocol of the Internet.
Routing Protocol Vectors/Categories
| Protocol | Category / Vector | Description |
| RIP (Routing Information Protocol) | distance-vector routing | Classified as an interior gateway protocol (IGP) Maximum hop count of only 15, and a single routing metric |
| IGRP (Interior Gateway Routing Protocol) | distance-vector routing | Considered a classful routing protocol IGRP supports multiple metrics for each route, including bandwidth, delay, load, MTU, and reliability Maximum hop count of IGRP-routed packets is 255 (default is 100) |
| EIGRP (Enhanced Interior Gateway Routing Protocol) | distance-vector routing | Adds support for VLSM (variable length subnet mask) Adds the Diffusing Update Algorithm (DUAL) in order to improve routing and provide a loopless environment. EIGRP has completely replaced IGRP |
| OSPF (Open Shortest Path First) | link-state routing protocol | Routes packets based solely on the destination IP address found in IP packets. Designed to support variable-length subnet masking (VLSM, CIDR). OSPF detects changes in the topology, such as link failures, very quickly and converges on a new loop-free routing structure within seconds. Falls into the group of interior gateway protocols, operating within an autonomous system (AS) The most widely-used interior gateway protocol (IGP) in large enterprise networks. OSPF does not use TCP or UDP but uses IP directly, via IP protocol 89. OSPF handles its own error detection and correction, therefore negating the need for TCP or UDP functions. |
| BGP (Border Gateway Protocol) | path vector protocol | Makes routing decisions based on path, network policies and/or rulesets. v4 supports Classless Inter-Domain Routing and the use of route aggregation to decrease the size of routing tables. RFC 4271 The most widely-used exterior gateway protocol (EGP) is BGP. |
Forwarding Techniques
Techniques to make the size of the routing table manageable.
- Next-Hop Method vs. Route Method
- The routing table holds only the address of the next hop instead of information about the complete route (route method).
- Network-Specific Method vs. Host-Specific Method
- Instead of having an entry for every destination host connected to the same physical network (host-specific method), we have only one entry that defines the address of the destination network (Network-Specific Method).
- Default Method
- Default routing is used to send packets with a remote destination network not in the routing table to the next hop router.
Loop Prevention with Routing Protocols
Split horizon in distance-vector Routing Protocols
- Split horizon is a loop-prevention method.
- When using split horizon, a routing protocol tries to prevent a routing loop, by not advertising a route from an interface from which it received an advertisement for that route.
- Simply: The split horizon rule prohibits a router from advertising a route through an interface that the router itself uses to reach that destination network.
Example: (Connect Router A & Router B via Network 4)
- Router A: Directly Connected Networks: 1, 2, 3, 4
- Router B: Directly Connected Networks: 4, 5, 6, 7
- Router B will not advertise networks 1, 2, or 3 back to Router A
- Router A will not advertise networks 5, 6, or 7 back to Router B
Protocols using split horizon
- RIP
- IGRP
- EIGRP
Poison Reverse
- Route poisoning, specifying a hop count greater than the maximum, is a method to prevent routing loops within computer networks.
- With RIP, the maximum hop count is 15, so to poison a route, a hop count of 16 is used.
- Distance-vector routing protocols in computer networks use route poisoning to indicate to other routers that a route is no longer reachable and should be removed from their routing tables.
- When a router gets an update with the poisoned route (hop 16) the route goes into a hold down state (where it remains in the route table with a metric of 16) for a period of 4 times the update interval. This value is known as the hold-down timer. If it doesn’t get an update with a non-infinite metric (less than 16 hops) within the hold down timer period it will remove the route from the routing table when the hold-down timer expires.
- RIP updates are 30 sec by default so a couple of minutes may pass before the route is removed.
Packet Lost on the Return Trip
- If the error occurs because of a known issue, such as if a route is not in the routing table on the way to the destination device, you will see an ICMP destination unreachable message.
- If the packet is lost on the way back to the originating host, you will typically see an ICMP request timed-out message because it is an unknown failure.
